SIGNIN
源码
1 | # -*- encoding: utf-8 -*- |
绕过
想要读取密钥就要绕过if '../../' in name or name.startswith('/') or name.startswith('../') or '\\' in name:
我们可以想到利用**./**进行绕过。
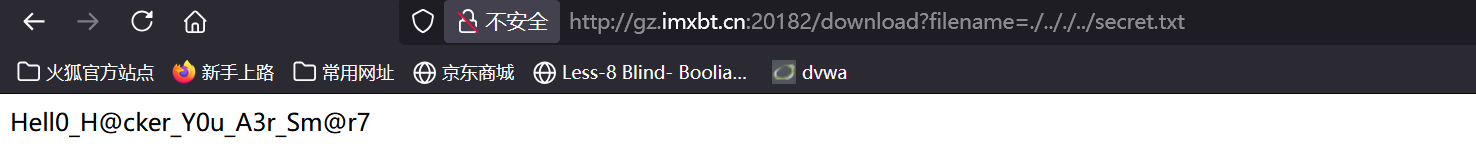
pickle反序列化
由
1 | def secret_page(): |
发现在get_cookie中有反序列化
1 | def get_cookie(self, key, default=None, secret=None, digestmod=hashlib.sha256): |
简单来说就是签名正确就能进行pickle的反序列化。
脚本如下:
1 | import hashlib |
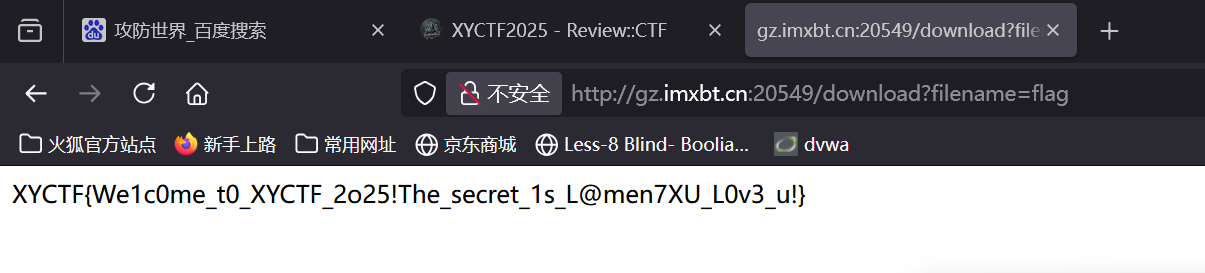
替换session后再用/download路由读取flag。
还有一个更简单的利用set_cookie函数的脚本
1 | from bottle import Bottle, request, response,run, route |
同上,然后访问app.py
就能得到flag